Picture this scenario: Your annual web-based training course has been completed, with various informational e-mails sent company-wide. Now the last step in your cybersecurity awareness program is to check off that box, for the regulators, and wait to do it again next year. It’s amazing how often we still see this check-the-box approach to cybersecurity awareness programs, with lenders failing to leverage their programs to maximize the potential cybersecurity benefits.
The cybersecurity profession has long preached that security controls must be built in layers, with no single “silver bullet” solution to address all risks. If this is the case, then why is the awareness program still just an afterthought—something that only happens each October, during National Cybersecurity Awareness Month. For cybersecurity to gain the necessary exposure throughout an organization and rise to the level of regular boardroom discussion, awareness programs must be built to include consistent communications and interaction among the cybersecurity team, business units, and senior leadership.
In this article we will address the business e-mail compromise (BEC) as a growing cyber threat to mortgage originations, and explore how a strong cybersecurity awareness program can defend against it.
BEC and Mortgage Origination Transactions
The BEC is a common phishing attack that deceives a target into changing the wiring instructions on a scheduled payment and diverting the funds to the attacker’s account. The requests are crafted in such a way that the e-mail appears to be originating from a trusted authority figure.
Historically, we have seen examples of the attacker sending an urgent, targeted e-mail to a recipient in a lender’s finance department, who is instructed by someone claiming to be the CEO to wire money to what is usually a trusted vendor. The attack uses enough accuracy for the e-mail to seem legitimate, but there are slight details that differ (for example, the sender’s e-mail address is off by a single letter, or the account number the money is being wired to is altered). The changes are subtle enough that an employee under the stress of an urgent request is unlikely to notice.
While this “classic” attack has garnered significant attention (and is likely the focus of many awareness programs), the mortgage industry has seen the BEC evolve beyond lenders to target third parties: customers, real estate agents, closing agents, and even warehouse lenders involved in mortgage transactions. In July 2018, the FBI reported a sharp rise in real estate scams using BEC and E-mail Account Compromise (EAC, for individuals’ accounts). “From calendar year 2015 to calendar year 2017, there was over a 1,100 percent rise in the number of BEC/EAC victims reporting the real estate transaction angle and an almost 2,200 percent rise in the reported monetary loss,” the FBI said. In May 2018 alone, nearly 120 cases were reported.
Third-party compromises usually take place at the customer, real estate agent, or closing agent level. E-mails are monitored by the attacker to identify the approaching transaction closing. On that day, a fraudulent e-mail is sent, stressing an urgent change to wiring instructions. The timing of the pending closing creates additional stress on the customer, who is worried about closing delays. This increases the likelihood the customer will just follow the instructions, rather than calling the real estate agent or lender to ask questions.
In the classic form of attack, on the lender itself, e-mail filters and other enterprise security tools can be configured to help detect and limit some of the BECs. In a third-party attack, however, enterprise controls will have no effect on customers and partners involved in the closing process of a mortgage transaction. This is where awareness programs and partnerships formed between lenders’ business units and cybersecurity teams provide additional strengths to help mitigate risk.
Building a Culture of Continuous Awareness
Effective and regular communications are not only key to an awareness program, but also serve as the foundation for the overall cybersecurity program. The bulk of the cybersecurity team’s interaction with business units or senior executives should not be driven by an annual national awareness month or by regulatory requirements. To maximize the effectiveness of cybersecurity communications, there should be a regular cadence of communications that ingrains a cybersecurity mindset into the fabric of an organization.
Keep in mind that a regular cadence doesn’t mean you send the same canned message on a quarterly basis. An effective, mature awareness program will use multiple delivery methods and actively tailor the message to the audience. Critical program components should involve the cybersecurity team in the following:
- Establishing standing meetings with key executives and/or board members outside of regular board meetings.
- Partnering with business units by attending department meetings to deliver job-specific cybersecurity tips relevant to their daily activities.
- Implementing phishing awareness tools to reinforce training messages throughout the year and help protect against active phishing threats.
- Creating posters, pamphlets, and desk aids that can serve as quick reminders and foster secure behaviors and actions specific to departments’ daily activities.
- Identifying cybersecurity champions outside of the cybersecurity team. Every organization has individuals just waiting to let out their “inner geek.” Their enthusiasm should be leveraged to create advocates throughout the business who help deliver the message and identify risks.
Even after establishing a multipronged approach to delivering the message, it’s critical that the message’s content is also tailored throughout the year. To demonstrate the value in a strong awareness program, let’s look at how tailored messaging can help reinforce controls to address classic and third-party BEC attacks.
The Value of a Reinforced Message
In any BEC attack, the threat and control techniques can vary greatly based on the role your organization plays in the origination process. Consider the participants in a complex mortgage origination transaction:
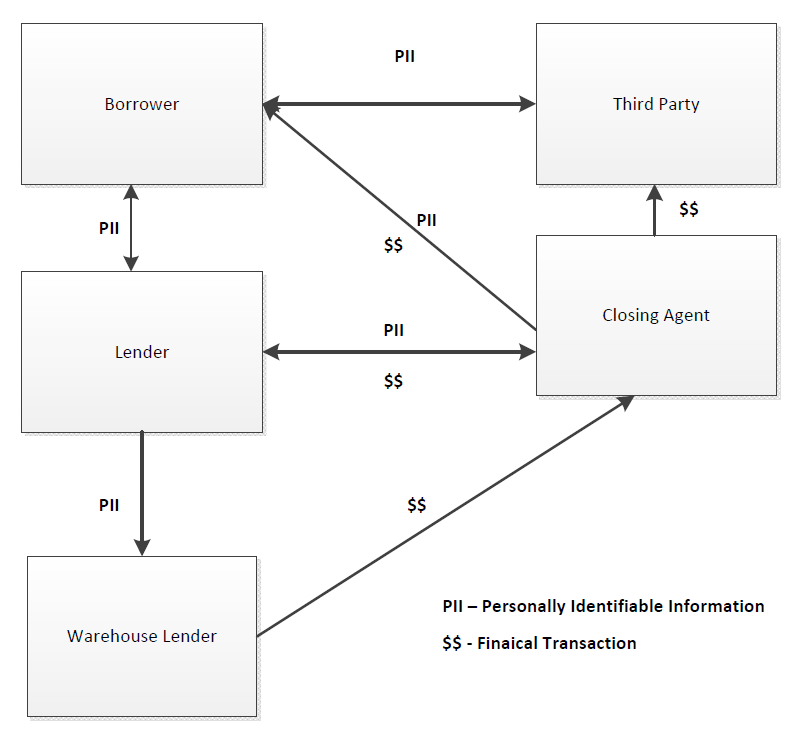
A BEC compromise presents a potential threat to almost all of the parties identified in the previous diagram. But how each party is affected varies greatly, as does the ability of each to mitigate the risk directly.
The lender in this scenario has the most ability to directly influence control, since it directly interacts with almost all of the participants. When dealing with the warehouse lender, controls can be implemented as the partnership is formed to define how secure interactions will be conducted. Processes can be documented, and formal language included in contracts. Additionally, e-mail filters and other enterprise security tools can be configured for both participants to detect and stop some of the e-mails, but the enterprise controls will have no effect on customers and partners involved in the closing process.
The interaction between the lender and warehouse lender is likely to be the easiest to secure, assuming a strong cybersecurity program at both organizations. But even with strong technical controls, BEC attacks can be effective at this level, because they target the weakest link in the control framework—the human element. This is where an effective continuous awareness program steps in to reinforce the controls.
Phishing Simulation Training
Typical annual awareness training programs will mention the threat of phishing attacks, and may even get into the details of the specific BECs we’ve described above. But the lesson is often forgotten as soon as employees reach the screen telling them they’ve passed the course.
Simulated phishing activities can further reinforce awareness messaging and also build engagement and ownership by employees. During such simulations, cybersecurity teams at the lender and warehouse lender create targeted e-mails simulating BEC attacks on the mortgage origination process. In addition, many phishing training platforms on the market today include plugins that enable a quick action button within your e-mail software, allowing employees to report suspected phishing attempts. Implementing such solutions not only allows cybersecurity teams to deliver a relevant message directly to those who would be targeted, but also empowers employees to actively report suspicious e-mails throughout the year.
Regular Communications and Department Meetings
Earlier we said that a key component of a mature awareness program is the establishment of regular communications among cybersecurity teams and business unit leaders and staff. Once established, it’s critical for the cybersecurity team to make messaging relevant to the business units they are addressing. The team should avoid reiterating the same canned message used in annual awareness e-mails or training.
Having this regular cadence enables the cybersecurity team to provide real-time updates when new threats emerge or activity increases. More importantly, the cybersecurity team’s presence lets employees on the front line provide feedback on what they are seeing and hearing from customers and vendors. These regular touchpoints serve as opportunities to build trust from both sides.
Mitigating Threats Outside of the Organization
As we stated earlier, the interaction between a lender and a warehouse lender is an easier point to secure, given the likely resources involved on both sides. But what happens if the attack is targeted outside of these two participants? Customers, real estate agents, and sometimes even closing agents have far fewer security resources to deploy, if any.
Again, we will turn to the lender as the central interaction hub. Enterprise cybersecurity tools and processes will be unable to protect entities outside of your organization. However, there are still processes and communications that can be shared with business units to mitigate these threats.
In the mortgage process, many documents are sent to customers with various instructions and information. To mitigate BEC attacks, cybersecurity and loan origination teams should work closely to inform customers how any changes during the process will be communicated. Make it clear that last-minute changes will not be communicated via e-mail and ensure that a phone number is provided for questions. Similar communications can be provided to real estate and closing agents. The goal, as with the awareness program, is to provide real-time information that is relevant to the transaction that is about to take place, to ensure the security message is fresh in participants’ minds.
Attackers Don’t Hibernate, Neither Should Your Cybersecurity Awareness Program
The examples we’ve used in this article focus on leveraging cybersecurity awareness programs to strengthen controls within the mortgage origination process. Regardless of your organization’s role in the process, BEC threats have the potential to hurt your operations. The importance and purpose of a continuous cybersecurity awareness program go far beyond regulatory compliance. Effective, mature programs provide additional strength to technical controls by securing the weakest link in any security program—the human.
